
Credit: This blog post is a reimagination of the chapter with a similar name in MITRE’s Ten Strategies of a World-Class Cybersecurity Operations Center. Their document is an invaluable resource and highly recommended reading, but as it was published in 2014, both the cyber threats that organizations are up against, as well as the defense tools available, have evolved. This article reimagines their advice to be more applicable in today’s cybersecurity landscape.
What is a SOC?
- Real-time monitoring, detection, and analysis of potential cyber incidents
- Incident response, including containment, eradication, and recovery
- Prevention of incidents through proactive activities, such as vulnerability scanning and remediation
With that said, many organizations may feel they are already doing these activities without a SOC.
It is common for businesses with an immature cybersecurity program to perform the above using an ad-hoc, decentralized SOC composed of members of its IT staff. If this is how your organization operates, it is imperative to ask the question: do we need our own SOC?
Do we need our own SOC?
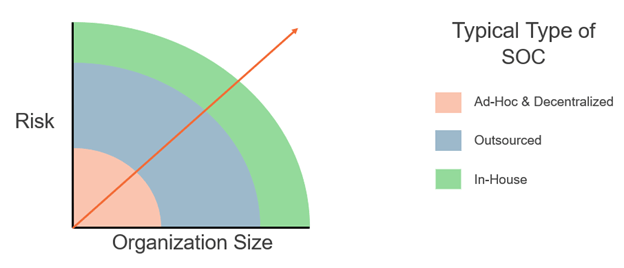
Not every organization needs its own SOC. With MSSPs offering affordable 24×7 SOC-as-a-service options, outsourcing can be a great option instead of building an in-house SOC or forgoing a SOC altogether. The chart below shows the typical type of SOCs that we see among organizations based on their size and the amount of inherent risk factors to their business model.
Evaluating your score
Below is a quick summary of how to evaluate your total score. Note that the score ranges and recommendations below are just guidelines, not hard and fast rules.
1 - 3 total points
VPLS Recommends
The organization can probably make do with an ad-hoc, decentralized approach to a SOC using members of the in-house IT staff, but an outsourced SOC is still recommended.
4 - 14 total points
VPLS Recommends
The organization probably doesn’t warrant its own SOC, but a SOC is necessary, so an outsourced SOC is recommended.
15+ total points
VPLS Recommends
An outsourced SOC may still work, but the organization should strongly consider its own SOC, especially if points are much higher than 15.
We notice organizations who fall between 1 and 3 points will typically try to perform SOC services using existing members of the IT staff due to budget constraints.
One word of caution here is that in this SOC model, there is significant risk that the incidents will go unnoticed by your team, especially when you consider incidents that happen after business hours. Even if they are noticed, there is still risk that those incidents won’t be dealt with in the most efficient, effective, or comprehensive manner.
Action items
- Assess your organization quantitatively using the worksheet
- Assess your organization qualitatively
- Compare the results – does your score match your perception?
VPLS provides a wide variety of cybersecurity services, including 24×7 SOC-as-a-service and professional services. If you would like to discuss all things SOC with VPLS, including our recommendation based on your SOC worksheet score results, then please contact us. Our staff of certified security experts are always ready and available to help.

Read More from this Author


