VPLS Expands Bare Metal and Cloud Platform into A New Singapore Data Center, Reinforces Presence in Southeast Asia
VPLS Expands Bare Metal and Cloud Platform into A New Singapore Data Center, Reinforces Presence in Southeast Asia
VPLS Expands Its Bare Metal & Cloud Platform into A New Singapore Data Center, Reinforces Presence in Southeast Asia
We are excited to announce the addition of a second Singapore data center location. The facility, known as SIN2, is located at 20 Ayer Rajah Crescent in Ayer Rajah Industrial Park in Singapore.
Home to the Asia-Pacific Network Operation Center (NOC), the SIN2 datacenter provides access to one of the world’s three GRX peering points, making it one of the most network-dense data centers in the region.
We are thrilled to further expand our hosting offerings with the Krypt.com bare metal and cloud brand into Southeast Asia by adding this new Singapore location,” states Mohamed Arab, VP of Cloud and Managed Services at VPLS. “The addition of SIN2 will allow customers in Asia and the Pacific Rim to further access the high-density, low-latency carrier network provided by the GRX Peering Point. With this new location, VPLS now manages over 68,000 VMs worldwide
Mohamed Arab, VP of Cloud and Managed Services
The SIN2 data center offers increased bandwidth capabilities to customers in Thailand, Indonesia, Hong Kong, and China, as well as the rest of Southeast Asia and Hawaii.
Queenstown, Singapore Data Center Highlights
- 181,716 sq. ft. near downtown Singapore
- Multi-stage security, including biometric sensors and proximity card readers
- N+1 redundant critical load generator standby power
- Access to 150+ carriers from the GRX Peering Point
Read More from this Author




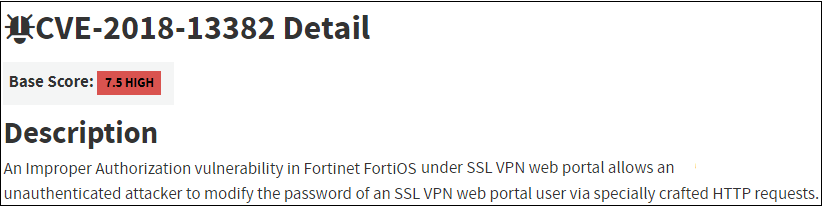
 A SOC, or Security Operations Center, is a group of security analysts organized to detect, analyze, respond to, report on, and prevent cybersecurity incidents. Sometimes going by other names, such as Computer Security Incident Response Team (CSIRT), this group is the organization’s focal point for security operations and computer network defense (CND).
A SOC, or Security Operations Center, is a group of security analysts organized to detect, analyze, respond to, report on, and prevent cybersecurity incidents. Sometimes going by other names, such as Computer Security Incident Response Team (CSIRT), this group is the organization’s focal point for security operations and computer network defense (CND).