
NSA TOOLS THREATEN CYBER SECURITY
Are you curious as to why the National Security Agency (NSA) is popping up all over your newsfeed? Well, you’re not alone! Many Americans are asking themselves the same question and wondering what this shadowy organization has to do with one of the largest exploits to cyber security history.
SHADOW BROKERS AND THE NSA
In 2016, a group known as Shadow Brokers released a variety of hacking exploits that were allegedly used by the NSA itself, called EternalBlue. The exploits contained a list of vulnerabilities to major firewall products and compromised IP addresses.
Initially, the group aimed to release the exploits in return for currency – Bitcoin. But, when the stunt failed to garner much attention (or funds), Shadow Brokers bid themselves farewell and released a second set of Microsoft Windows-related vulnerabilities.
ETERNALBLUE AND RANSOMWARE
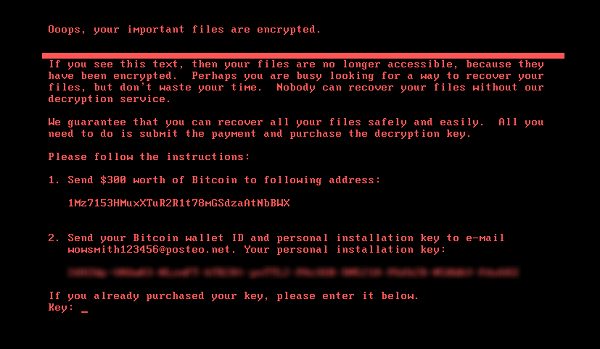
A form of malicious software, ransomware limits control of a user’s system and/or data unless a ransom is paid. In more advanced versions, the ransomware will encrypt data files and only grant access with a decryption key. Typically, hackers will request payment in the form of cryptocurrency, as it offers its holders anonymity.
Only a month after the leak of EternalBlue, new strains of ransomware hit organizations across the globe, most commonly known as WannaCry, Petya, and WannaMine.
Here’s a peek at what an unlucky user would see on their screen:
PETYA
WANNACRY
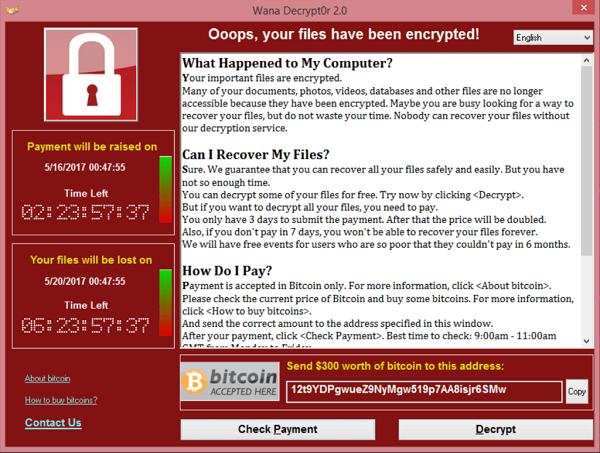
In general, ransomware such as WannaCry works in the following way:
- User accidentally runs a malicious code (perhaps downloaded from an email attachment).
- Ransomware encrypts files on the user’s hard drive.
- When prompted, the user is left with a countdown in which payment in the form of Bitcoin is then demanded. As time goes on, the ransom payment increases.
- After a set amount of time, if the ransom is not paid, all encrypted data files are lost.
Are you panicking, yet?
NSA TOOLS AND MICROSOFT WINDOWS
As if there wasn’t enough to worry about, further vulnerabilities have recently been exposed.
Researcher Sean Dillon, also known as ‘zerosum0x0’ on GitHub and Twitter, noted the vulnerabilities affects numerous versions of unpatched Windows Operating Systems.
https://twitter.com/zerosum0x0/status/957839430777057280
The exploit includes Microsoft’s most recent OS, Windows 10.
Again, these exploits affect UNPATCHED versions of Windows OS, so there should be little reason to worry, right?
NOPE.
Software updates are boring and no one likes waiting for them to finish.
If you agree with the above statement, then you most definitely have reason to worry.
Additionally, companies that use older versions of Windows may choose not to update because of compatibility issues with other software.
HOW CAN I PROTECT MYSELF AND MY PRECIOUS DATA?
Let’s go over some basic tips on what ordinary people, like you and me, can do in the fight against malware:
- Concerned about losing precious data? Back it up. In fact, most Windows and Mac OS products offer automatic backups, tailored to your schedule.
- Software updates are essential. Set software updates to download and install automatically.
- Suspicious email? Don’t open it.
- Stay up-to-date on the latest cyber security news. (If you’re still reading this, you’re already tackling one of the hardest steps!)
VPLS IS HERE TO HELP!
For 24/7 security service, check out VPLS’ Security Services with Fortinet and find out how you can keep your systems and data safe from hackers!
Don’t forget to share this article with friends! For more information, visit our blog and stay current with the latest news.
